Capture The Flag - Necromancer. Practicing my penetration testing skills to hack a target machine. Here's my test environment in my own private virtual network.
I setup my Kali Linux in host virtual network and my target machine (Necromancer) which I downloaded a OVA image from VulnHub website.
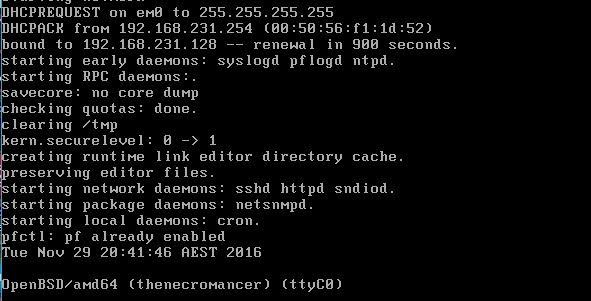
When I started my Kali Linux virtual machine, I have an assigned IP Address 192.168.231.129. This most likely a different IP address when you setup your own private network. And my target machine Necromancer IP address is 192.168.231.128. I saw this when I started the Necromancer virtual machine. This save me some time to scan all /24 within my network.
Anyway, if you still want to scan your network you can use "netdiscover" tool. If you're not sure what options to use simply run "netdiscover --help". Okay, got it? Now run # netdiscover -r 192.168.231.0/24 [Enter] to scan your private network. Here's the result of my network. I run "ifconfig" in my Kali to know the assigned IP address, then the other IP most likely for my target network.
192.168.231.1 00:50:56:c0:00:01 1 60 VMware, Inc.
192.168.231.128 00:0c:29:a5:8c:67 1 60 VMware, Inc.
192.168.231.129 00:50:56:f0:0a:96 1 60 VMware, Inc.
192.168.231.128 00:0c:29:a5:8c:67 1 60 VMware, Inc.
192.168.231.129 00:50:56:f0:0a:96 1 60 VMware, Inc.
With this information I can simply run nmap to my target IP address.
Note: IP Address renewal in 900 seconds.
Now my private network, Kali and target machine are ready. Let's begin hacking my target machine.
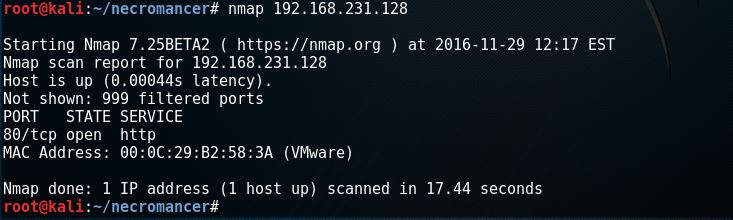
From Kali Linux virtual machine run # nmap 192.168.231.29 to see what I can discover.
I found port 80 open and 1 host up. That's a good start. Let's run # nmap -sU -n -r -T4 192.168.231.128
Now it's getting interesting. I found UDP port 666 a service for doom.
Let's fire up netcat using the newly discovered UDP port 666 # nc 192.168.231.128 666 [Enter].
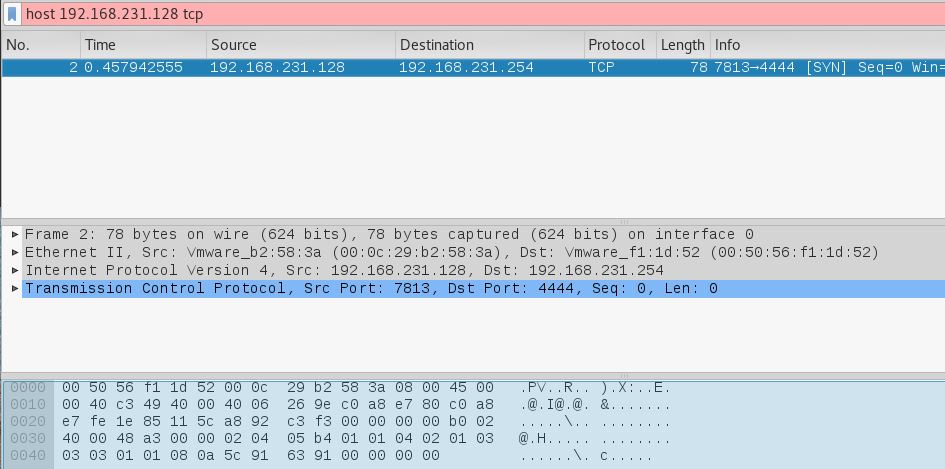
Hmm. Nothing happen. I wonder what's going on in the background. One way to find out, let's run our network snipping tool wireshark. I filter the result using my target machine IP Address 192.168.231.128 and found out it is trying to connect to the destination port 4444.
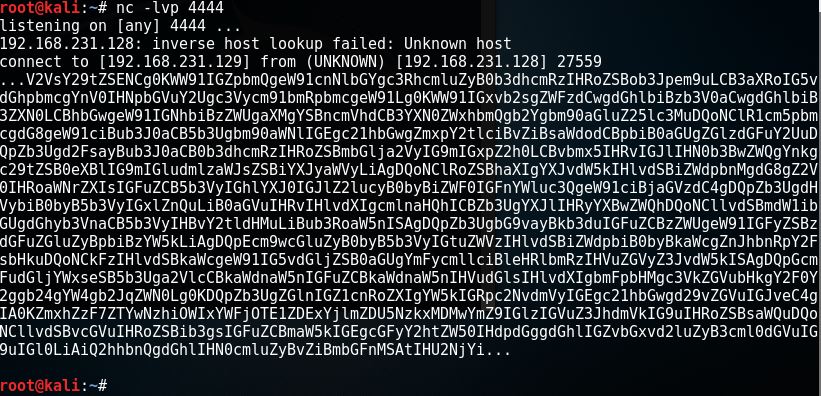
I open another terminal window, and setup to listen using port 4444 # nc -lvp 4444 [Enter]. And re-run # nc -u 192.168.231.128 666 [Enter], then wait to see the output in listening terminal window.
This is the result.
My first guess, it is a base64 code. I copied the code to my dumptext.txt file. And run #base64 -d -i dumptext.txt [Enter]
Woohh. I got the first flag.
I copied flag1{e6078b9b1aac915d11b9fd59791030bf} to my flags.txt file for recording purpose, just like a trophy :)
continue reading at QUE.COM - https://que.com/2016/11/30/ctf-necromancer/
Thank you.










0 Comments