FYI Android users, you have to read this article courtesy by HelpNetSecurity.com if you're an Android smart phone user. I actually read it first from CNN website and again today.
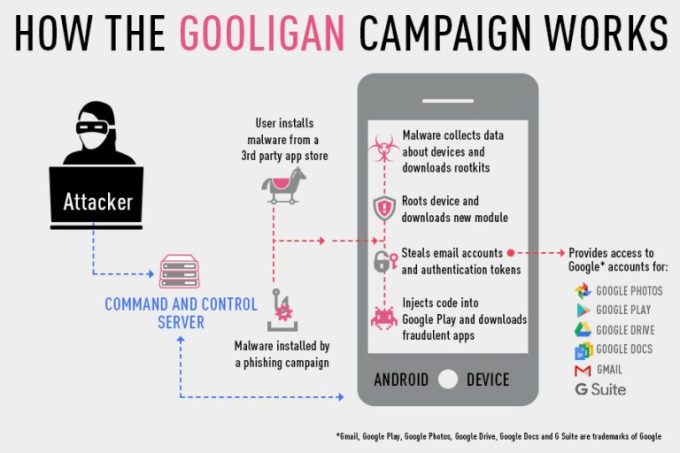
Check Point security researchers have revealed a new variant of Android malware, breaching the security of more than one million Google accounts.
Key findings
- The campaign infects 13,000 devices each day and is the first to root over a million devices.
- Hundreds of email addresses are associated with enterprise accounts worldwide.
- Gooligan targets devices on Android 4 (Jelly Bean, KitKat) and 5 (Lollipop), which represent nearly 74% of Android devices in use today.
- After attackers gain control over the device, they generate revenue by fraudulently installing apps from Google Play and rating them on behalf of the victim.
- Every day Gooligan installs at least 30,000 apps on breached devices, or over 2 million apps since the campaign began.
Check Point reached out to the Google security team immediately with information on this campaign. “As part of our ongoing efforts to protect users from the Ghost Push family of malware, we’ve taken numerous steps to protect our users and improve the security of the Android ecosystem overall,” stated Adrian Ludwig, Google’s director of Android security.
continue reading at Que.com website.
Sponsored by Retune.com






0 Comments