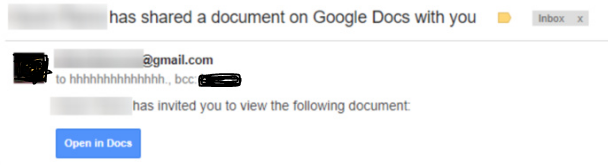
Another day of Email Phishing Attack, this one for Gmail user’s account as the target. Last Tuesday May 3, an email phishing attack that was designed to trick users into giving up access to their Gmail accounts started showing up on target email inbox. The 1st captured image below is an example of Gmail Phishing attack email. When a user click on the “Open in Docs” link, the hacker will exploit the Gmail user’s account.
But it did not stop there, this phishing attack also behave as a “worm” that also sent itself out to all the affected user’s contacts. The 2nd captured image is an example of email coming from @gsa.gov infected user’s contact. You might receive a similar email coming from different email addresses.
Please note the recipient email address “hhhhhhhhhhh@mailnator.com”, I hope this is enough reason not to open or read this message, delete it right away. If you clicked on the link and enter your Gmail credentials please continue to read on how to perform Google security check-up.
Here’s how to check your Gmail account.
- Open a new browser. I highly recommend using a modern browser e.g. Edge, Google Chrome or Firefox because they are equipped with safe browser features to protect and block malicious site or links.
- Login to your Gmail account. Check your Gmail account connected Apps here (https://myaccount.google.com/u/1/permissions?pli=1). Review and cancel any connection if you don’t need it or don’t know it.
- Go to Google Security Check-up (https://myaccount.google.com/secureaccount) to check your account.
I hope that help. Have a Safe surfing.
Source: QUE.com







0 Comments